Ssl Setup Apache Windows Sso
Nov 30, 2017. Integrated Windows authentication is most frequently used within intranet environments since it requires that the server performing the authentication and the user being authenticated are part of the same domain. For the user to be authenticated automatically, the client machine used by the user must also.
To view all attacks, please see the page. Last revision (mm/dd/yy): 10/6/2015 Overview A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder.
By manipulating variables that reference files with “dot-dot-slash (./)” sequences and its variations or by using absolute file paths, it may be possible to access arbitrary files and directories stored on file system including application source code or configuration and critical system files. It should be noted that access to files is limited by system operational access control (such as in the case of locked or in-use files on the Microsoft Windows operating system). This attack is also known as “dot-dot-slash”, “directory traversal”, “directory climbing” and “backtracking”. Related Security Activities How to Avoid Path Traversal Vulnerabilities See the article on how to Vulnerabilities. How to Test for Path Traversal Vulnerabilities See the article on how to Vulnerabilities. Description Request variations Encoding and double encoding:%2e%2e%2f represents./%2e%2e/ represents./.%2f represents./%2e%2e%5c represents.%2e%2e represents..%5c represents.%252e%252e%255c represents..%255c represents. Percent encoding (aka URL encoding) Note that web containers perform one level of decoding on percent encoded values from forms and URLs..%c0%af represents./.%c1%9c represents.
OS specific UNIX Root directory: “ / “ Directory separator: “ / “ WINDOWS Root directory: “: “ Directory separator: “ / “ or “ ” Note that windows allows filenames to be followed by extra. / characters. In many operating systems, null bytes%00 can be injected to terminate the filename. For example, sending a parameter like:?file=secret.doc%00.pdf will result in the Java application seeing a string that ends with '.pdf' and the operating system will see a file that ends in '.doc'. Attackers may use this trick to bypass validation routines. Examples Example 1 The following examples show how the application deals with the resources in use.
In these examples it’s possible to insert a malicious string as the variable parameter to access files located outside the web publish directory. Dir/some file dir/some file The following URLs show examples of *NIX password file exploitation. Note: In a windows system an attacker can navigate only in a partition that locates web root while in the Linux he can navigate in the whole disk. Example 2 It's also possible to include files and scripts located on external website.
Example 3 These examples illustrate a case when an attacker made the server show the CGI source code.
Authentication Authentication verifies a user's identity. Everyone who needs to access Tableau Server—whether to manage the server, or to publish, browse, or administer content—must be represented as a user in the Tableau Server identity store.
The method of authentication may be performed by Tableau Server (“local authentication”), or authentication may be performed by an external process. In the latter case, you must configure Tableau Server for external authentication technologies such as Active Directory, SAML, or OpenID. In all cases, whether authentication takes place locally or is external, each user identity must be represented in the Tableau Server identity store, which is managed by the. Access and management permissions are implemented through site roles. Site roles define which users are administrators, and which users are content consumers and publishers on the server.
For more information about administrators, site roles, groups, Guest User, and user-related administrative tasks, see and. Note: In the context of authentication, it’s important to understand that users are not authorized to access external data sources through Tableau Server by virtue of having an account on the server. In other words, in the default configuration, Tableau Server does not act as a proxy to external data sources. Such access requires additional configuration of the data source on Tableau Server or authentication at the data source when the user connects from Tableau Desktop. User identity in Tableau Server When you install Tableau Server, you must select the process that the server will use to manage user authentication: local authentication or Active Directory. Before you install Tableau Server, you should understand how these two options impact your overall authentication strategy.
After you select and set the authentication process, Tableau Server will configure the various components for the authentication method that you have selected. After this configuration is complete, you cannot change the authentication method. In fact, to change this configuration, you must uninstall the server, delete the configuration on the computer, and then reinstall the server. Local authentication If the server is configured to use local authentication, then the Tableau Server identity store is used exclusively to authenticate users.
Free Antivirus Software For Retired Military. When users sign-in and enter their credentials, either through Tableau Desktop, tabcmd, API, or web client, Tableau Server verifies the credentials. To enable this scenario, you must first create an identity for each user. To create an identity, you specify a username and a password. To access or interact with content on the server, users must also be assigned a site role. User identities can be added to Tableau Server in the server UI, using, or using the. You can also create groups in Tableau Server to help manage and assign roles to large sets of related user groups (e.g., “Marketing”).
Use local authentication if any of the following are true: • Your organization does not manage users with Active Directory • You do not want to use Active Directory • You want to use OpenID for authentication and single sign-on When you configure Tableau Server for local authentication, you cannot set password policies or account lockout on failed password attempts. If you require these account safeguards, then you should use Active Directory authentication. Active Directory If Tableau Server is configured to use Active Directory authentication, then credentials are managed and verified by Active Directory. When a user logs onto Tableau Server from Tableau Desktop or a web client, the credentials are passed through to Active Directory, which then verifies them and sends an access token to Tableau Server. Tableau Server will then manage user access to Tableau resources based on the site roles stored in the local identity store.
In this scenario, Tableau Server must be installed in a domain in Active Directory. Tableau Server will sync user and group metadata from Active Directory to the identity store. You do not have to manually add users. However, after the data is synchronized, you will need to assign site and server roles. You can assign these individually, or at the group level.
Tableau Server does not synchronize any data back to Active Directory. Ultra Focus Keygen Download Bandicam more. Tableau Server manages content and server access according to the site role permission data is stored in the repository. If you are already using Active Directory to manage users in your organization, then we recommend selecting Active Directory authentication during Tableau setup to make user provisioning and management easier. For example, by synchronizing Active Directory groups, you can set minimum site role Tableau permissions for users that are synchronized in the groups.
You can synchronize specific Active Directory groups, or you can synchronize them all. For more information, see.
Be sure to review to understand how multiple domains, domain naming, NetBIOS, and Active Directory user name format influence Tableau user management. Single sign-on options for Tableau Server Tableau Server supports several types of single sign-on (SSO) solutions. With SSO, users don't have to explicitly sign in to Tableau Server. Instead, the credentials they've used to authenticate already (for example, by signing in to your corporate network) are used to authenticate them to Tableau Server, and they can skip the step of entering a username and password to access Tableau Server. With SSO, the user's identity as established externally is mapped to a user identity defined in the Tableau Server identity store.
When you configure Tableau Server to use an SSO solution, all authentication is handled by the SSO solution. However, Tableau Server will manage user access to Tableau resources based on the site roles stored in the identity store. Tableau Server supports these types of SSO: • SAML.You can configure Tableau Server to use SAML (security assertion markup language) for SSO. With SAML, an external identity provider (IdP) authenticates the user's credentials, and then sends a security assertion to Tableau Server that provides information about the user's identity. You can use SAML to access Tableau Server if you have configured Active Directory or local authentication on Tableau Server. For more information, see.
If Kerberos is enabled in your environment and if the server is configured to use Active Directory authentication, you can provide users with access to Tableau Server based on their Windows identities. You cannot use Kerberos if your Tableau Server is configured for local authentication.
For more information, see. OpenID Connect is a standard authentication protocol that lets users sign in to an identity provider (IdP) such as Google. After they've successfully signed in to their IdP, they are automatically signed in to Tableau Server.
To use OpenID Connect on Tableau Server, the server must be configured to use local authentication. Active Directory authentication is not supported. For more information, see.
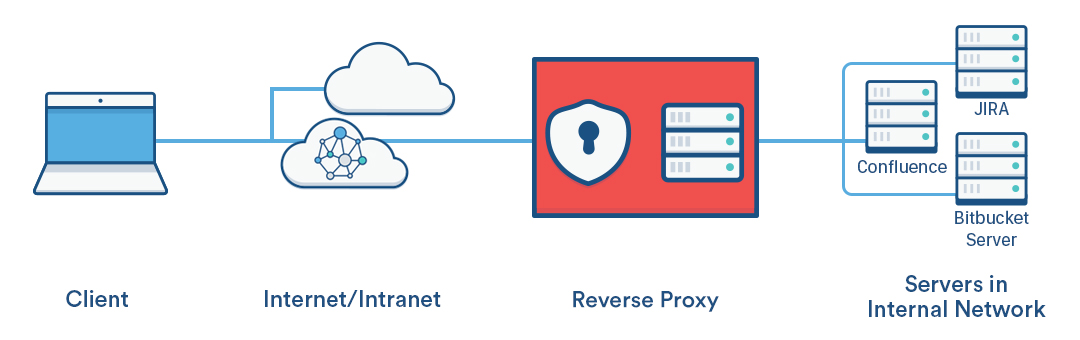
• Trusted Authentication. Trusted authentication lets you set up a trusted relationship between Tableau Server and one or more web servers. When Tableau Server receives requests from a trusted web server, it assumes that the web server has already handled whatever authentication is necessary. Tableau Server receives the request with a redeemable token or ticket and presents the user with a personalized view which takes into consideration the user’s role and permissions.
For more information, see. • Integrated Windows Authentication.
If you have configured Tableau Server with Active Directory authentication, you can enable automatic logon. Automatic logon uses Microsoft SSPI to sign in your users based on their Windows username and password. Users are not prompted for credentials, which creates an experience similar to single sign-on (SSO). To enable automatic login see,. Related topics • • REST API.